🚀 Introducing Content API MFA & Email 2FA
Protect Your Strapi App with Real MFA
Headlockr now supports Content API MFA & Email 2FA. Boost your Strapi security with true multi-factor authentication—built for serious developers.
In today's digital landscape, securing your content management system (CMS) is more critical than ever. With sensitive data at stake, robust authentication mechanisms are essential to protect against unauthorized access.
At Headlockr, we recognize this imperative. That's why we're excited to announce the launch of Content API Multi-Factor Authentication (MFA) and Email 2FA—enhancements designed to fortify your Strapi environment.
🔐 The Rising Threat of Credential-Based Attacks
Credential-based attacks are a growing concern. According to IBM's 2024 Cost of a Data Breach report, compromised credentials were the leading initial attack vector, accounting for 16% of breaches. These breaches are not only prevalent but also costly, with the average data breach reaching nearly $4.9 million—a 10% increase from the previous year.
For developers building digital products with Strapi, implementing robust authentication is no longer optional—it's a necessity.
🧠 What Is Headlockr?
Headlockr is a powerful MFA plugin tailored for Strapi. It enhances API security by offering flexible authentication methods:
- SMS-based MFA
- Time-Based One-Time Passwords (TOTP)
- Backup codes
- Email 2FA (newly added)
With Headlockr, you can customize security levels to meet specific needs, ensuring both administrators and developers maintain control over access.
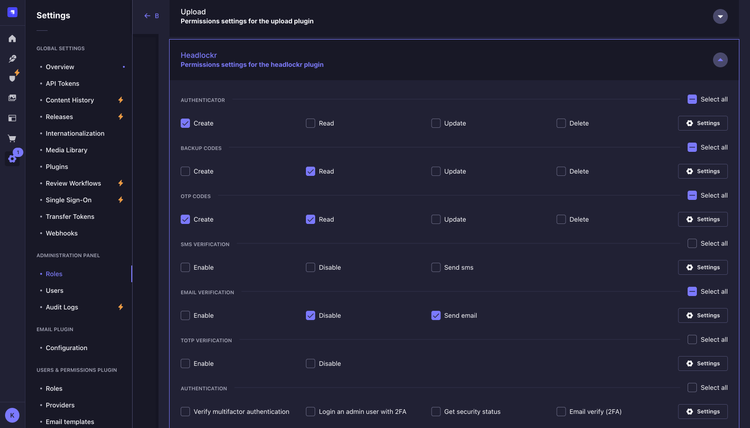
🆕 New Features: Content API MFA & Email 2FA
Previously, Headlockr supported MFA exclusively for the Strapi admin panel. We're now extending this security to the Content API, enabling end-to-end MFA protection across your entire application.
Key features include:
- Enable/Disable MFA methods: Choose between email, SMS, or TOTP-based MFA.
- Phone: Register and verify your phonenumber within Strapi
- Send OTP: Send otp/totp codes via all of our supported MFA methods
- Backup codes: Generate and manage backup codes for account recovery.
- Administrator controls: Globally enforce or disable MFA policies for both the admin panel and Content API.
With these enhancements, you can integrate Headlockr into any frontend framework— be it Next.js, Vue, Svelte, Remix, Nuxt, or React—thanks to our frontend-agnostic API.
💡 Why This Matters
Let’s face it—many community-built plugins for authentication in Strapi focus on getting things to “just work.” While that’s a great starting point, they often lack the depth, attention to edge cases, and robust security design required in production environments. These solutions frequently overlook critical concerns like token isolation, permission enforcement, rate limiting, and secure cryptographic handling.
At Headlockr, we approached this differently.
We didn’t want to build “just another MFA plugin.” We wanted a bulletproof solution that can stand up to real-world attacks, compliance standards, and the demands of growing tech teams. That’s why we invested significant effort into:
- A deep native integration with Strapi’s permission engine
- Achieving comprehensive end-to-end security for both the Content API and the Admin Panel.
- True isolation between admin and content APIs, with separate tokens, cookies, and secrets
- Full role-based access control (RBAC) support for API-level enforcement
- Secure fallback options like backup codes, and best-practice cryptography
- A frontend-agnostic API that works across every framework without compromise
This isn’t a bolt-on solution. It’s a foundational layer for serious developers, digital agencies, and organizations that treat security as a non-negotiable part of their stack.
So while others patch together partial solutions, we’ve built Headlockr from the ground up with a singular goal: real security that you can trust.
The addition of Email 2FA completes our suite of commonly used MFA methods. We're also exploring advanced authentication options, including:
- Biometric login: Utilize Face ID or Touch ID on devices.
- Passkeys: Embrace passwordless login methods.
- Companion app: Receive push notifications for authentication challenges, similar to GitHub mobile.
⚙️ Developer-Friendly Configuration
Our latest update focuses on future-proofing and compliance with standards like ISO 27001 and SOC 2. We've integrated Headlockr natively with Strapi's permission engine, offering:
- Role-Based Access Control (RBAC): Define access policies per role.
- Configurable settings: Manage rate limiting, JWT token options, cookie settings, and more via a straightforward plugins/config.js file.
To maintain a clear separation between the admin panel and Content API, all tokens, cookies, and secrets are individually signed and encrypted. This ensures that credentials for one API do not grant access to the other.
🛡️ How We Align with ISO 27001 & SOC 2
While Headlockr itself is not a certified product, we’ve designed it in alignment with key security controls and principles from ISO 27001 and SOC 2 Type II standards. These frameworks define what "good security hygiene" looks like—and Headlockr helps your Strapi setup get closer to that benchmark.
🔍 Alignment highlights:
✅ Access Control (ISO 27001 Annex A.9 / SOC 2 CC6.1)
Headlockr enforces strict authentication policies through MFA (SMS, TOTP, Email), and role-based access rules. You control who gets access to what—both in the Admin Panel and via the Content API.
✅ Authentication Strengthening (ISO A.9.4.2 / SOC 2 CC6.2)
We support strong authentication factors, minimize reliance on single credentials, and isolate authentication flows between APIs to reduce attack surfaces.
✅ Cryptographic Controls (ISO A.10 / SOC 2 CC6.7)
All tokens, cookies, and secrets are signed and encrypted using modern, secure algorithms. No shared secrets between APIs.
✅ Security Configuration Management (ISO A.12.1.2 / SOC 2 CC7.1)
With a centralized config.js, all security settings (JWT, cookies, rate limits) are version-controlled, auditable, and environment-specific—supporting reproducible secure deployments.
✅ Protection Against Brute-Force Attacks (SOC 2 CC7.2)
We include rate limiting on authentication endpoints and track invalid login attempts to help mitigate credential stuffing and abuse.
📦 Use Cases & Integrations
The new features allow businesses to integrate MFA into any tech stack. Whether you've built a login system with Next.js, Remix, Nuxt, or React, Headlockr integrates seamlessly. Our API's frontend-agnostic design ensures compatibility across frameworks.
Looking ahead, we plan to release starter kits and an SDK to expedite the integration process, minimizing time to production while offering customization flexibility.